Bypass or Disable UAC for Selected Excluded Programs Only with Elevator (SkipUAC)
It’s possible to completely turn off and disable UAC (User Account Control, commonly misspelled as User Access Control) in Windows Vista, or make it elevate to highest privileges automatically and silently without user noticing whenever such administrator’s level privileges are required and requested. But it’s impossible to disable UAC or force Windows Vista to exclude or ignore UAC security protection for selected applications or programs only.
User Account Control provides security protection for system kernel, memory and registry from unauthorized access by programs or processes. But at times, there are programs that are frequently used, and always trusted to run safely in admin privilege granted highest priority mode. For example, command prompt (Cmd) session, Windows Management Console (MMC), Registry Editor (RegEdit), System Configuration Utility (MsConfig) and etc.
As UAC doesn’t have exclusion list, User Account Control dialog will always pop up each and every time these programs is ran to request for permission to elevate to run on highest privileges level or priority. Encountering such dialog many times is pretty useless and troublesome. Elevator, written by Martin Zugec, adds new “Elevate me” entry to right click context menu for all files and shortcuts, and will skip and bypass UAC elevation prompt to directly launch the program in high priority admin privilege mode, without having require users to shut or turn off UAC feature on their systems.
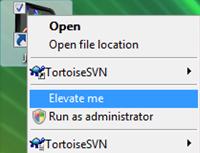
“Elevate me” right click context menu points to ElevateRunner which creates configuration in ElevateThis task container, and then Elevator will call Scheduled Task function in Windows Vista, which has the option to let user specify that scheduled task to be run using highest privileges, to parse through ElevateThis folder and run anything in it.
To install Elevator, unpack “SkipUAC.zip” and then run Install.cmd as Administrator. To uninstall, simply run Uninstall.cmd at the same folder.
If you are loathing still having to right click on a program or shortcut icon to skip or bypass the UAC elevation request for a program, it’s possible to change shortcut to always run the pointed program in elevation mode using Elevator. The hack is to modify shortcut’s target to run ElevatorRunner.exe with filename and parameters to the executable to automatically open as Administrator mode.
For example, to always run a Command Prompt shortcut in elevation high privilege mode without asking for permission to continue (suppressing to skip or bypass the UAC prompt), simply set the Target field of the shortcut to ElevatorRunner Cmd. Of course, you may need to specify full path to ElevatorRunner.exe. For example, C:\SkipUAC\ElevatorRunner.exe %SystemRoot%\system32\cmd.exe.
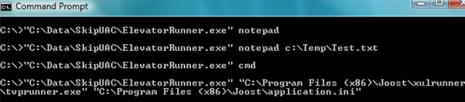
Other than define directly in shortcut’s properties, the same command can also called from Run textbox or command prompt. ElevatorRunner.exe accepts 2 parameters. First parameter is executable to run and second parameter is any command line arguments to include when running the executable.
Recent Articles
- How To Download HBO Shows On iPhone, iPad Through Apple TV App
- Windows 10 Insider Preview Build 19025 (20H1) for PC Official Available for Insiders in Fast Ring – Here’s What’s News, Fixes, and Enhancement Changelog
- Kaspersky Total Security 2020 Free Download With License Serial Key
- Steganos Privacy Suite 19 Free Download With Genuine License Key
- Zemana AntiMalware Premium Free Download For Limited Time